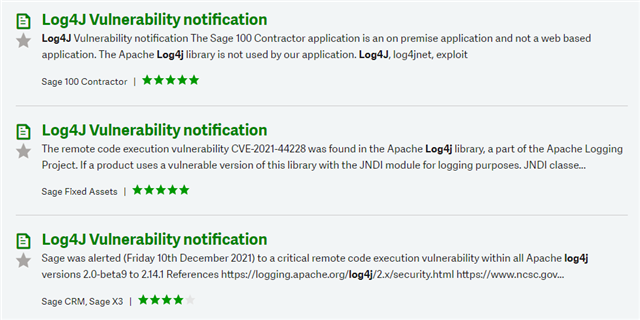
Last week a proof of concept for a vulnerability around Log4j was distributed on the Internet. New zero-day exploit for Log4j Java library is an enterprise nightmare (bleepingcomputer.com)
Almost immediately bad actors started trying to exploit the vulnerability. Hackers start pushing malware in worldwide Log4Shell attacks (bleepingcomputer.com)
Is the Sage 100 server vulnerable to the Log4j vulnerability? What impact would this have on Sage 100?