Hi Readers,
Today’s blog posting will be a short review of the new features / changes made to the installation process for our latest release of 2023R2 (12.0.34). All of these changes you will find are located within the Sage X3 Management Console (aka SAFE Console). Let’s take a peek, shall we?
First up are the updates to SQL Server Module. As we learned in our previous release, SQL Server Module 22 was not yet compatible. Well, it is now! When updating to 2023R2 make sure you are updating the SQL Server Module to 22.1.1 for the PowerShell requirements. You can look for my previous blog on SQL Server Module to learn how to update it or check out the link at the end of the blog. (Also to note, if you install the SQL Server 2022 SE or EE you will get SQL Server Module 22.1.1)
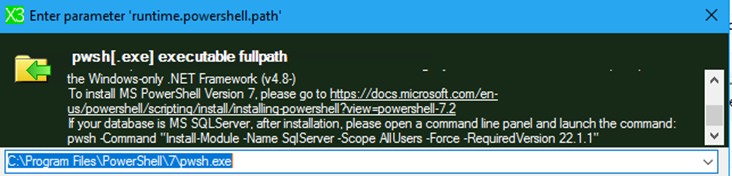
Next up, we have some additions to Runtime component in the way of Connection Security. Two new security settings for the runtime connectivity have been added to the Management Console in 2023 R2:
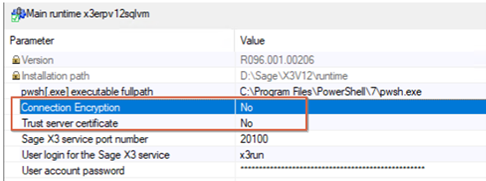
The first one you will notice is “Connection Encryption”. This specifies whether the connection to the database is TLS encrypted. If this is enabled and “Trust Server Certificate” is set to no, SQL Server will require a valid trusted certificate chain. You can install the certificates through a PowerShell script that the Console will provide (Action menu). If “Trust Server Certificate” is set to Yes, SQL Server will trust the connection by default and no additional certificate is needed.
The second one you will see is the “Trust server certificate”. If you set this option to ‘Yes’ the RT will bypass the TLS/SSL certificate chain validation for the SQL Server database connection. In this case, the connection will be trusted by default. When this is set to 'No', the certificate chain will be controlled by SQL Server and will require valid certificates to be installed. To Note: The 'No' value is recommended on production instances for maximum security. If your certificate chain is not valid, SQL Server will issue an error stating that the certificate chain is not trusted.
Lastly, there is a new Action Menu option called “Save SQL Server Certificate Creation Script”. This was added to support the new "Trust server certificate" setting. It does exactly what it says, when you click on it, it will ask you to download a ps1 script.
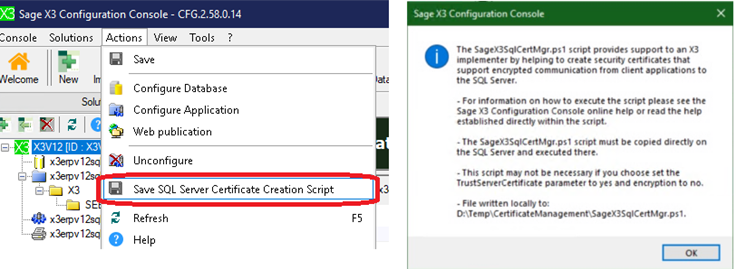
Here’s a brief look at what the download script looks like:
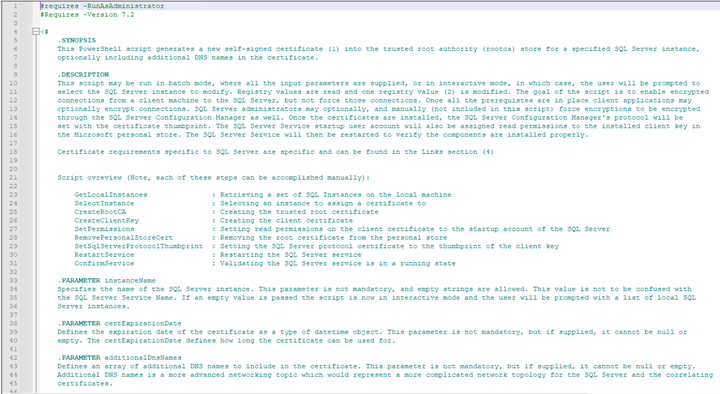
The purpose of this is to help create a self-signing certificate that you can use if you do not have one currently to use.
As you can see the synopsis says:
“ This PowerShell script generates a new self-signed certificate (1) into the trusted root authority (rootca) store for a specified SQL Server instance, optionally including additional DNS names in the certificate.”
To learn more about this certificate configuration you will see “.LINK” sections throughout the script to help with understanding the process. I have located them all and added them below:
- https://learn.microsoft.com/en-us/powershell/module/pki/new-selfsignedcertificate?view=windowsserver2022-ps
- https://learn.microsoft.com/en-us/sql/relational-databases/security/networking/tds-8?view=sql-server-ver16#strict-connection-encryption
- https://learn.microsoft.com/en-us/sql/database-engine/configure-windows/certificate-requirements?source=recommendations&view=sql-server-ver16#certificate-requirements-for-sql-server-encryption
- https://docs.microsoft.com/en-us/dotnet/api/system.environment.newline?view=net-6.0
- https://learn.microsoft.com/en-us/sql/database-engine/configure-windows/certificate-requirements?view=sql-server-ver16
IMPORTANT NOTE: Before you use this option, SQL Server will need to be properly configured to take advantage of these new settings.
You can find more information on this subject by visiting our Online Help!
Until next time,
SQL Server Module Blog: Installing SqlServer Module 21.1.18256 (because v22.0.59 breaks stuff)

